Secretariat for 2023 G20 Summit
For Prelims: G20 and its members, Location of G20 countries.
For Mains: Importance of G20, India’s role in G20, Groupings & Agreements Involving India and/or Affecting India's Interests.
Why in News?
Recently, the Union Cabinet set in motion the process to build a Secretariat that will look after the affairs of organising the G20 summit in 2023.
- India will steer the international body as its President from 1st December 2022 to 30th November 2023, which will lead to the G20 summit to be hosted here.
- The Secretariat will be functional till February 2024. It will also enable long term capacity building, including knowledge and expertise, for India’s leadership on global issues in multilateral fora.
- Indonesia assumed the Presidency of G20 in December, 2021.
What is G20?
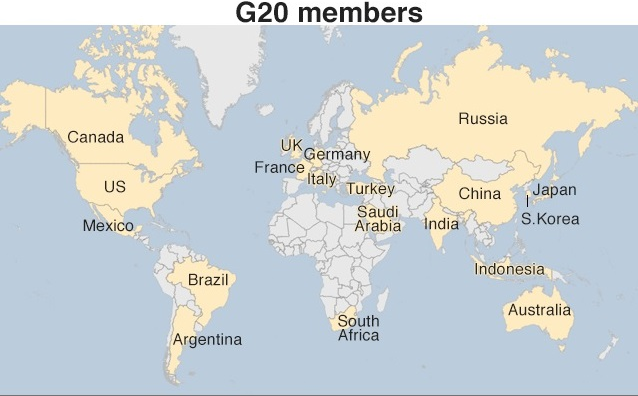
- It is an informal group of 19 countries and the European Union (EU), with representatives of the International Monetary Fund and the World Bank.
- It does not have a permanent secretariat or Headquarters.
- The membership comprises a mix of the world’s largest advanced and emerging economies, representing about two-thirds of the world’s population, 80% of global Gross Domestic Product (GDP), 80% of global investment and over 75% of global trade.
- Its members are Argentina, Australia, Brazil, Canada, China, France, Germany, India, Indonesia, Italy, Japan, Republic of Korea, Mexico, Russia, Saudi Arabia, South Africa, Turkey, the United Kingdom, the United States and the EU.
- Each G20 country is represented by its Sherpa, who plans, guides, implements, etc. on behalf of the leader of their respective country.
- Current Commerce and Industry Minister is the current “G20 Sherpa” of India.
How G20 Evolved?
- The Global Financial Crisis (2007-08) cemented G20’s reputation as the premier crisis management and coordination body.
- The US, which held the G20 Presidency in 2008, elevated the meeting of the Finance Ministers and Central Bank Governors to Heads of State, resulting in the first G20 Summit.
- The Summits in Washington DC, London, and Pittsburgh set the scene for some of the most durable global reforms:
- Blacklisting states in an effort to tackle tax evasion and avoidance, provisioning stricter controls on hedge funds and rating agencies, making the Financial Stability Board an effective supervisory and watchdog body for the global financial system, proposing stricter regulations for too-big-to fail banks, refraining members from imposing new barriers to trade etc.
- By the time Covid-19 struck, the G20 had wandered off from its original mission and G20 lost its focus.
- G20 reinvented itself by widening its agenda to include issues such as climate change, jobs and social security issues, inequality, agriculture, migration, corruption, terror financing, drug trafficking, food security and nutrition, disruptive technologies, and meeting the sustainable development goals.
- In recent times, G20 members have made all the right commitments after the pandemic, but there is little to show in action.
- At the Riyadh Summit in October 2020, they prioritised four things: fighting the pandemic, safeguarding the global economy, addressing international trade disruptions, and enhancing global cooperation.
- The Italian Presidency in 2021 had focused on three broad, interconnected pillars of action — People, Planet, Prosperity — vowing to take the lead in ensuring a swift international response to the pandemic.
- Despite millions of deaths, the G20 members have refused to give the legal backing to manufacture vaccines in developing countries.
What is India’s Potential for the G20 Presidency?
- As a founding member of the G20, India has used the platform to raise issues of vital importance and those that impact on the most vulnerable around the world.
- But due to the rising toll of unemployment rates and poverty in the domestic portion, it’s hard to take the lead effectively.
- India has set a strong example as the only country among G20 nations that is on track towards meeting what it had promised in 2015 Paris Agreement in terms of being the only 2 degree Celsius compatible country and is much ahead as compared to other G20 countries in terms of fulfilling this commitment.
- Concurrently, India’s leadership role in delineating the success of India-France led International Solar Alliance is globally well acclaimed as a turning point intervention in mobilising resources towards promoting research and development in renewable energy.
- Also, the vision of ‘Self Reliant India (Atmanirbhar Bharat)’ initiative is expected to play a transformational role for “New India” in the global paradigm as an important and reliable pillar of world economy and global supply chains in the aftermath of Covid -19 crisis.
- India’s endeavour of establishing the Coalition for Disaster Resilient Infrastructure, comprising nine of the G20 nations amongst others provides new dimensions of leadership in the global growth process.
Way Forward
- G20 needs leaders with impeccable global credentials. With India to assume the Presidency in 2022 it has the opportunity to restore the world's faith in multilateralism.
- The emerging economies, along with the US, must make equitable vaccine rollout and patent waiver the number one priority for G20.
- The G20 must strengthen the partnership with international organisations such as the IMF, the OECD, the WHO, the World Bank and the WTO, and delegate them the task of monitoring progress.
National Supercomputing Mission
For Prelims: Param Pravega, Supercomputer, National Supercomputing Mission, National Knowledge Network (NKN).
For Mains: National Supercomputing Mission, IT and Computers, Achievements of Indians in Science & Technology.
Why in News?
Recently, the Indian Institute of Science (IISc) Bengaluru installed the supercomputer 'Param Pravega'. It has a supercomputing capacity of 3.3 petaflops.
- It has been installed under the government’s National Supercomputing Mission.
- The National Supercomputing Mission is intended to indigenise the development and manufacturing of powerful computers.
What is a Supercomputer?
- A supercomputer is a computer that performs at or near the currently highest operational rate for computers.
- Generally, PETAFLOP is a measure of a Supercomputer’s processing speed and can be expressed as a thousand trillion floating point operations per second.
- FLOPS (floating point operations per second) are typically used to measure the performance of a computer’s processor.
- Using floating-point encoding, extremely long numbers can be handled relatively easily.
- Supercomputers are primarily designed to be used in enterprises and organizations that require massive computing power.
- For example: weather forecasting, scientific research, intelligence gathering and analysis, data mining etc.
- Globally, China has the maximum number of supercomputers and maintains the top position in the world, followed by the US, Japan, France, Germany, Netherlands, Ireland and the United Kingdom.
- India’s first supercomputer was PARAM 8000.
- PARAM Shivay, the first supercomputer assembled indigenously, was installed in IIT (BHU), followed by PARAM Shakti, PARAM Brahma, PARAM Yukti, PARAM Sanganak at IIT-Kharagpur, IISER, Pune, JNCASR, Bengaluru and IIT Kanpur respectively.
- In 2020, PARAM Siddhi, the High-Performance Computing-Artificial Intelligence (HPC-AI) supercomputer, achieved global ranking of 62nd in Top 500 most powerful supercomputer systems in the world.
What is the National Supercomputing Mission?
- In 2015, the National Supercomputing Mission was launched to enhance the research capacities and capabilities in the country by connecting them to form a Supercomputing grid, with National Knowledge Network (NKN) as the backbone.
- The NKN project is aimed at establishing a strong and robust Indian network which will be capable of providing secure and reliable connectivity.
- It supports the government's vision of 'Digital India' and 'Make in India' initiatives.
- The Mission is being jointly steered by the Department of Science and Technology (DST) and the Ministry of Electronics and Information Technology (MeitY).
- It is implemented by the Centre for Development of Advanced Computing (C-DAC), Pune, and the IISc, Bengaluru.
- The mission was planned in three phases:
- Phase I looking at assembling supercomputers,
- Phase II looking at manufacturing certain components within the country.
- Phase III where a supercomputer is designed by India.
- An indigenously developed server platform called ‘Rudra’ is being tried out in a pilot system, with an interconnect for inter node communication called Trinetra also having been developed.
Border Infrastructure and Management
For Prelims: Border Infrastructure & Management, Border Area Development Programme.
For Mains: Significance of Border Infrastructure & Management in Securing Borders.
Why in News?
Recently, the Ministry of Home Affairs has approved the continuation of the Central Sector Umbrella Scheme of “Border Infrastructure and Management” (BIM) over the 15th Finance Commission Cycle from 2021-22 to 2025-26, at a cost of Rs.13,020 crore.
What does BIM Envisage?
- The BIM scheme will help in the creation of infrastructure such as border fence, border flood lights, technological solutions, border roads and Border OutPosts (BOPs) and company operating bases to secure India's borders with Pakistan, Bangladesh, China, Nepal, Bhutan and Myanmar.
- It will strengthen the border infrastructure for improving border management, policing and guarding the borders.
- India's border with Pakistan is 3,323 km long, including about 775 km of the Line of Control. The length of the border is 4,096 km with Bangladesh, 3,488 km with China, 1,751 km with Nepal, 699 km with Bhutan, 1,643 km with Myanmar.
What are the other Initiatives to Secure Borders?
- Vibrant Villages Programme:
- Border villages with sparse population, limited connectivity and infrastructure often get left out from the development gains. Such villages on the northern border will be covered under the new Vibrant Villages Programme, announced in the Budget 2022-23.
- The activities will include construction of village infrastructure, housing, tourist centers, road connectivity, provisioning of decentralized renewable energy, direct to home access for Doordarshan and educational channels, and support for livelihood generation.
- The move has been taken to counter the Chinese 'model villages' close to the LAC (Line of Actual Control).
- It will be an improved version of the existing border area development programme.
- The Border Area Development Programme:
- BADP was initiated in the border areas of the western region during the Seventh Five Year Plan (1985-90), for ensuring balanced development of border areas through development of infrastructure and promotion of a sense of security among the border population.
- The programme aims to meet the special development needs of the people living in remote and inaccessible areas situated near the international border and to saturate the border areas with the essential infrastructure through convergence of Central/State/BADP/Local schemes and participatory approach.
- Smart Fencing in India (CIBMS):
- Two pilot projects covering about 71 Kms on Indo-Pakistan Border (10 Kms) and Indo-Bangladesh Border (61 Kms) of Comprehensive Integrated Border Management System (CIBMS) have been completed.
- CIBMS involves deployment of a range of state-of-the-art surveillance technologies — thermal imagers, infra-red and laser-based intruder alarms, aerostats for aerial surveillance, unattended ground sensors that can help detect intrusion bids, radars, sonar systems to secure riverine borders, fibre-optic sensors and a command and control system that shall receive data from all surveillance devices in real time.
- BOLD-QIT (Border Electronically Dominated QRT Interception Technique) under CIBMS on the Indo- Bangladesh border in Dhubri district of Assam is also being used.
- Two pilot projects covering about 71 Kms on Indo-Pakistan Border (10 Kms) and Indo-Bangladesh Border (61 Kms) of Comprehensive Integrated Border Management System (CIBMS) have been completed.
- Border Road Organization:
- Founded in 1960, the organisation plays a major role in providing defense infrastructure including roads, bridges, highways, airports, tunnels, buildings and other such structures.
- BRO. has constructed lifelines of over 53,600 km for the people of Sikkim, Arunachal Pradesh, Mizoram, Manipur, Nagaland, Tripura, Meghalaya, Ladakh, Jammu & Kashmir, Uttarakhand, Himachal Pradesh and Andaman & Nicobar Islands.
A Gist of Border Infrastructure Development |
|||
| Main Threat | What needs to be done? | What has been done? | |
| Pakistan | War, insurgency, smuggling. | C.I.B.M.S. monitoring with a well-trained and larger BOLD-QIT, more than one route connecting far flung areas, especially Jammu and Kashmir | C.I.B.M.S. in some stretches, 3rd route to Leh to be opened by 2023. |
| China | War | Armored vehicle capable infrastructure, high altitude airfields. | Daulet Beg Oldie airfield running, some bridges and tunnels armored vehicle capable. |
| Bangladesh | Smuggling, human trafficking | C.I.B.M.S. monitoring with BOLD-QIT throughout including riverine stretches | Brahmaputra river covered, rivulets still remaining. |
| Nepal | Smuggling, human trafficking | C.I.B.M.S. monitoring with BOLD-QIT | Planning stage. |
| Bhutan | Smuggling | Armored vehicle capable road connectivity till Bhutan-China border. | B.R.O. working on it. |
| Myanmar | Smuggling, insurgency, trafficking. | C.I.B.M.S. monitoring with bigger and more efficient BOLD-QIT to tackle insurgency, roads for swift troop movements | Some roads present. C.I.B.M.S. planning stage. |
Quantum Key Distribution Technology
For Prelims: Quantum Key Distribution Technology, Quantum Technology and its applications, Qubits.
For Mains: Quantum Key Distribution Technology and its benefits and needs, applications of quantum technology.
Why in News?
Recently, a joint team of scientists from Defence Research and Development Organisation (DRDO) and Indian Institute of Technology (IIT) Delhi, for the first time in the country successfully demonstrated Quantum Key Distribution link between Prayagraj and Vindhyachal in Uttar Pradesh, a distance of more than 100 kilometres.
- With this success, the country has demonstrated indigenous technology of secure key transfer for bootstrapping military grade communication security key hierarchy.
- Earlie, China’s satellite Micius had sent light particles to Earth to establish the world’s most secure communication link.
What is Quantum Key Distribution Technology?
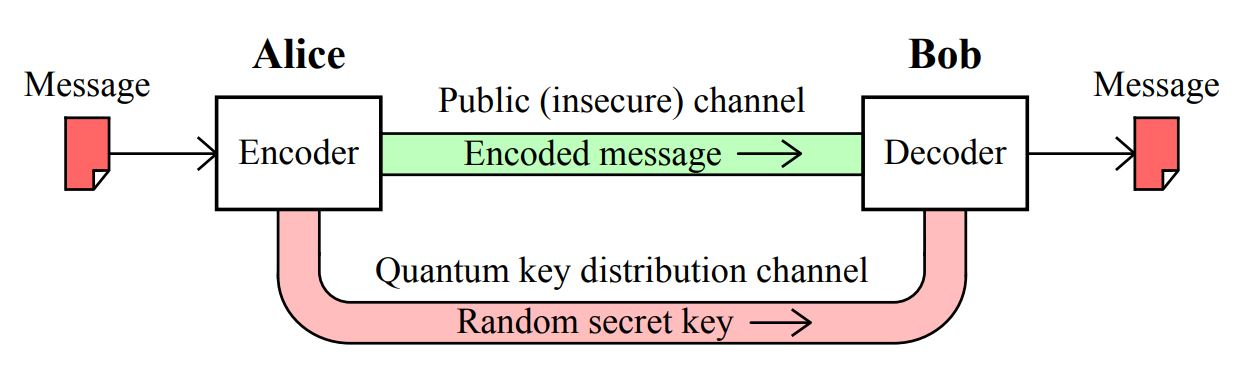
- QKD, also called Quantum Cryptography, is a mechanism to develop secure communication.
- It provides a way of distributing and sharing secret keys that are necessary for cryptographic protocols.
- Cryptography is the study of secure communications techniques that allow only the sender and intended recipient of a message to view its contents.
- Cryptographic algorithms and protocols are necessary to keep a system secure, particularly when communicating through an untrusted network such as the Internet.
- The conventional cryptosystems used for data-encryption rely on the complexity of mathematical algorithms, whereas the security offered by quantum communication is based on the laws of Physics.
What are the Two Main Categories of QKD?
- Prepare-and-Measure Protocols:
- It focuses on measuring unknown quantum states. This type of protocol can be used to detect eavesdropping (spying), as well as how much data was potentially intercepted.
- Entanglement-based Protocols:
- It focuses on quantum states in which two objects are linked together, forming a combined quantum state.
- The concept of entanglement means that measurement of one object thereby affects the other. In this method, if an eavesdropper accesses a previously trusted node and changes something, the other involved parties will know.
How does the Quantum Key Distribution Work?
- In the QKD, encryption keys are sent as ‘qubits’ (or quantum bits) in an optical fibre.
- Qubits -- the equivalent of bits in a binary system.
- Optical fibers are capable of transmitting more data over longer distances and faster than other mediums. It works on the principle of total internal Reflections.
- QKD implementation requires interactions between the legitimate users. These interactions need to be authenticated. This can be achieved through various cryptographic means.
- QKD allows two distant users, who do not share a long secret key initially, to produce a common, random string of secret bits, called a secret key.
- The end-result is that QKD can utilize an authenticated communication channel and transform it into a secure communication channel.
- It is designed in a way that if an illegitimate entity tries to read the transmission, it will disturb the qubits – which are encoded on photons.
- This will generate transmission errors, leading to legitimate end-users being immediately informed.
Why is QKD Needed?
- QKD is essential to address the threat that rapid advancement in Quantum Computing poses to the security of the data being transported by various critical sectors through the current communication networks.
- Quantum Technologies can broadly be divided into four verticals viz. Quantum Computing, Quantum Communications, Quantum Sensors and Quantum Materials.
- The technology would be useful in enabling various start-ups and small and medium enterprises in the domain of quantum information.
- It will enable security agencies to plan a suitable quantum communication network with indigenous technology backbone.
- The encryption is unbreakable and that’s mainly because of the way data is carried via the photon.
- A photon cannot be perfectly copied and any attempt to measure it will disturb it. This means that a person trying to intercept the data will leave a trace.
What are the Challenges associated with the QKD?
- Integration of QKD Systems into Current Infrastructure:
- For now, it is currently difficult to implement an ideal infrastructure for QKD.
- QKD is perfectly secure in theory, but in practice, imperfections in tools like single photon detectors create many security vulnerabilities.
- Distance in which Photons Can Travel:
- Modern fiber optic cables are typically limited in how far they can carry a photon. Commonly, this range is seen to be upward of 100 km.
- Use of QKD:
- QKD relies on already having a classically authenticated channel of communications established.
- This means that one of the participating users has probably already exchanged a symmetric key in the first place, creating a sufficient level of security.
- A system can already be made sufficiently secure without QKD through using another advanced encryption standard.
- However, as the use of quantum computers becomes more frequent, the possibility that an attacker could utilize quantum computing's ability to crack into current encryption methods rises -- making QKD more relevant.
- QKD relies on already having a classically authenticated channel of communications established.
Way Forward
- The power of startups and Big Tech corporations involved in developing quantum technology and applications must be harnessed.
- The focus should be to develop an overarching strategy for the next 10-15 years. The strategy must ensure that there is no misallocation of resources and that the efforts put in are concentrated in key areas that provide both economic and strategic benefits.
Animation, Visual Effects, Gaming and Comics (AVGC) Sector
For Prelims: AVGC Sector.
For Mains: AVGC Sector, its importance and related issues, Government policies & interventions.
Why in News?
In the Budget 2022-23, the government announced to set up ‘Animation, Visual Effects, Gaming and Comics’ (AVGC) task force to “build domestic capacity to serve Indian markets and global demand.”
- Earlier, the Karnataka High Court delivered a judgement striking down major portions of the Karnataka Police (Amendment) Act, 2021 which banned online gambling and skill-based gaming platforms.
- In 2021, the Ministry of Information and Broadcasting in collaboration with IIT Bombay decided to form a Centre of Excellence in gaming and other related areas.
What is the importance of the AVGC Sector?
- Play Larger Role in Meeting Global Demand:
- It will prepare India to play a larger role in building Metaverse, help in catering to the Indian market and in meeting global demand.
- A metaverse is a network of 3D virtual worlds focused on social connection and it can be defined as a simulated digital environment that uses Augmented Reality (AR), Virtual Reality (VR), and blockchain, along with concepts from social media, to create spaces for rich user interaction mimicking the real world.
- It could also open up new avenues for players and platforms as well as formalise game art education since most in the industry learn experientially.
- It will prepare India to play a larger role in building Metaverse, help in catering to the Indian market and in meeting global demand.
- Contribution in Revenue:
- The number of gamers in India grew to about 400 million by mid of 2020 from about 250 million gamers at the end of fiscal year 2018-19.
- This makes it the second largest base of online gamers in the world after China.
- Online casual gaming, which forms a large chunk of the total gaming revenue, is projected to grow at a Compound Annual Growth Rate (CAGR) of about 29% over the next four years to reach revenues of Rs 169 billion by FY25.
- Employment Generation:
- The potential for job opportunities in the AVGC sector is humongous.
- The number would vary between around 70,000 to 1.2 lakh job opportunities for the entire space.
What are issues with the AVGC Sector?
- No Formalisation:
- The AVGC sector is growing rapidly but there’s a void for good programmers, graphic designers or esports managers because there are no formal gaming courses.
- Regulatory Issues:
- Regulatory clarity continues to be a bug bear for the space as various State governments have dragged these companies to court over allegedly being akin to gambling.
- This is something that these companies have vehemently denied saying they are not 'games of chance' but rather 'games of skill.'
- Regulatory clarity continues to be a bug bear for the space as various State governments have dragged these companies to court over allegedly being akin to gambling.
Way Forward
- There needs to be an equal amount of Central and State participation to ensure regulatory clarity comes out in this space.
- The task force should look into aspects such as how to build capacities, how to embed this into education systems to build more future capabilities.
- It is necessary to find ways to formalise some of the education in this sphere, so that the country has animators, designers and people who can conceptualise, code and create those games and environments from India.
Draft India Data Accessibility & Use Policy 2022
For Prelims: Data Accessibility Policy, High Value Data, India Data Office, Data Protection Law.
For Mains: Government Policies & Interventions, Cyber Security, IT & Computers, Data Accessibility Policy and its Challenges.
Why in News?
Recently, the Ministry of Electronics and Information Technology (MeitY) released a policy proposal titled as, “Draft India Data Accessibility & Use Policy, 2022”.
- The policy objectives mentioned in this draft are primarily commercial in nature. It aims to radically transform India’s ability to harness public sector data.
- Earlier, a government committee headed by Infosys co-founder Kris Gopalakrishnan has suggested that non-personal data generated in India be allowed to be harnessed by various domestic companies and entities.
Why has the Draft Data Accessibility Policy been Proposed?
- Increased Data: The generation of citizen data is slated to increase exponentially in the next decade and become a cornerstone of India’s USD 5 trillion-dollar digital economy.
- Benefits of Data Exploitation: The National Economic Survey, 2019 noted the commercial benefits of Government data exploitation.
- The private sector may be granted access to select databases for commercial use.
- Absence of Policy: A background note that accompanies the policy outlines existing bottlenecks in data sharing and use.
- It includes the absence of a body for policy monitoring and enforcement of data sharing efforts, absence of technical tools and standards for data sharing, identification of high value datasets and licensing and valuation frameworks.
- To Unlock High Value Data: It indicates a way forward to unlock the high value of data across the economy, congruent and robust governance strategy, making Government data interoperable and instilling data skills and culture.
What are the Major Proposals of the Draft Data Accessibility Policy?
- India Data Office: The document proposes the establishment of an India Data Office (IDO) to streamline and unify data access and sharing among government and other stakeholders.
- It will define frameworks for high-value data sets, finalise data standards and metadata standards and review policy implementation, among others.
- Every ministry or department should have Data Management Units, headed by Chief Data Officers, which will work closely with the IDO to ensure the implementation of this policy.
- Coverage: All data and information generated, created, collected, or stored by the central government and authorised agencies shall be covered by the policy. The measures can also be adopted by state governments.
- Restricted Data: All government data will be open and shareable unless it falls under a negative list of data sets.
- Data categorised under the negative list of datasets that won’t be shared, and restricted access and shared only with trusted users, as defined by the respective ministry or department, under the controlled environment.
- Data Toolkit: All ministers or departments will receive a data-sharing toolkit to help assess and manage risk associated with data sharing and publication.
- The framework will assist data officers in determining whether a data set qualifies for release, restricted sharing, or must be placed on the negative list, as well as the proper release channel and degree of anonymity required.
- Aligned to Existing Laws: Data shall remain the property of the agency/ department/ ministry/ entity which generated/collected it. Access to data under this policy shall not be in violation of any acts and rules of the government of India in force.
- The legal framework of this policy shall be aligned with various acts and rules covering the data.
What are the Issues with the Draft Data Accessibility Policy?
- Privacy: India does not have a data protection law (Data Protection Bill) that can provide accountability and remedy for privacy violations such as coercive and excessive data collection or data breaches.
- Here, inter-departmental data sharing poses concerns related to privacy since the open government data portal which contains data from all departments may result in the creation of 360 degree profiles and enable state-sponsored mass surveillance.
- Even though the policy considers anonymisation as a desired goal there is a lack of legal accountability and independent regulatory oversight.
- There is also a failure to consider scientific analysis and the availability of automated tools for the re-identification of anonymous data.
- The commercial value of the data increases with greater amounts of personal data. The absence of an anchoring legislation further leads to the policy not being able to fulfil the threshold of legality for state intervention into privacy which was put in place by the Supreme Court of India in its landmark right to privacy decision (K.S. Puttaswamy v. Union of India i2017).
- Here, inter-departmental data sharing poses concerns related to privacy since the open government data portal which contains data from all departments may result in the creation of 360 degree profiles and enable state-sponsored mass surveillance.
- Transparency: While adopting the language of open data it strays from its core principle of providing transparency of the Government towards its citizens.
- There is only one mention of transparency and little to no mention of how such data sharing will help ensure demands for accountability and redress.
- Perverse Revenue Objective: The second issue is that the policy bypasses parliament as it contemplates large scale data sharing and enrichment that will be borne from public funds.
- Further, the constitution of offices, prescription of standards that may be applicable not only to the Central government, but even State governments and schemes administered by them require legislative deliberation.
- Federalism: The policy, even though it notes that State governments will be, “free to adopt portions of the policy,” does not specify how such freedom will be achieved.
- It becomes relevant, if specific standards are prescribed by the Central government for data sharing, or as a precondition to financial assistance.
- There is also the absence of any comment on whether data gathered from States may be sold by the Central government and whether the proceeds from it will be shared with the States.
- Lack of Clarity on Definitions for Key Concepts: New concepts introduced by the Policy have been defined in a vague and ambiguous manner which opens them up to misinterpretation.
- The Policy creates a separate category of ‘High-Value Datasets’ which it deems essential for governance and innovation, access to which will be accelerated.
- However, nowhere in the Background Note or the Policy has the category been concisely defined.
Saltwater Crocodile
Why in News?
Saltwater Crocodiles (Crocodylus porosus), used to be found in Vietnam and southern China, became extinct in these areas due to human activity.
What do we know about the Saltwater Crocodile?
- About:
- It is the largest of the 23 species of ‘extant’ or living crocodilians. This includes ‘true crocodiles’, alligators and caimans.
- The saltie is also called the ‘estuarine crocodile’ and as the name suggests, is typically found in the brackish water of estuaries.
- It can also tolerate saltwater in the oceans and can travel long distances over the open ocean, making use of tidal currents.
- Habitat:
- The ‘saltie’ is today found in three locations in India — the Sundarbans, Bhitarkanika National Park and the Andaman and Nicobar Islands.
- It is one of the three crocodiles native to the Indian Subcontinent, along with the mugger crocodile (Crocodylus palustris) and the gharial (Gavialis gangeticus).
- It is also found in Bangladesh, Malaysia, Indonesia, Brunei, the Philippines, Papua New Guinea, Australia and the Solomon Islands.
- During antiquity the species’ range extended from the Seychelles and Kerala, India in the west through to southeastern China, Palau and Vanuatu in the east.
- Threats:
- Habitat destruction, fragmentation, and transformation, fishing activities and use of crocodile parts for medicinal purposes.
What is the protection Status of Saltwater Crocodiles?
- IUCN List of Threatened Species: Least Concern
- CITES: Appendix I (except the populations of Australia, Indonesia and Papua New Guinea, which are included in Appendix II).
- Wildlife Protection Act, 1972: Schedule I
Exercise Eastern Bridge VI
Why in News?
Recently, the Indian Air Force (IAF) and the Royal Air Force of Oman began a five-day bilateral exercise at the Jodhpur air force station. The exercise is named Eastern Bridge VI, as is in its sixth edition.
- The exercise seeks to promote professional interaction, exchange of experiences and enhancement of operational knowledge, besides strengthening bilateral relations between the two countries.
- The Exercise Eastern Bridge V was held in October 2019 at the Air Force Base Masirah, Oman.
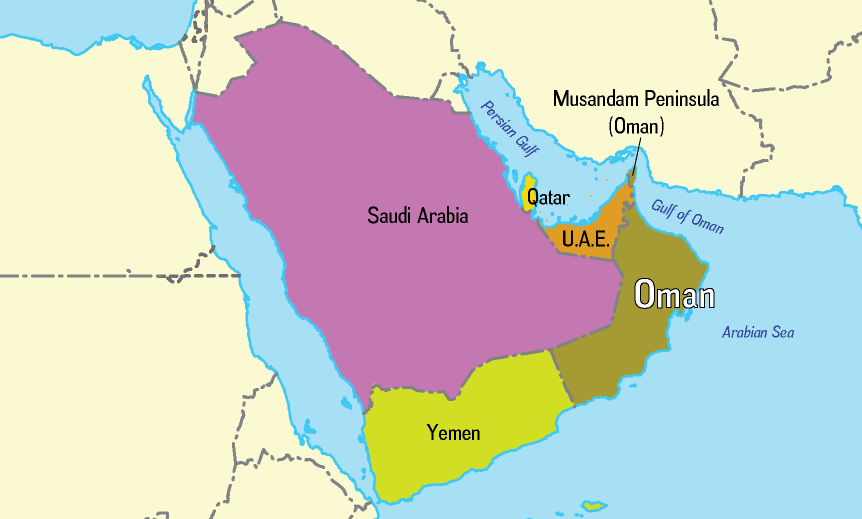
What is Oman’s Strategic Significance for India?
- About:
- Oman is India’s closest defence partner in the Gulf region and an important anchor for India’s defence and strategic interests.
- Oman is at the gateway of Strait of Hormuz through which India imports one-fifth of its oil imports.
- Defence cooperation has emerged as a key pillar for the robust India-Oman strategic partnership. Defence exchanges are guided by a Framework MOU which was recently renewed in 2021.
- Oman is the only country in the Gulf region with which all three services of the Indian armed forces conduct regular bilateral exercises and staff talks, enabling close cooperation and trust at the professional level.
- Naseem Al-Bahr is the naval exercise conducted between both the countries.
- AL Nagah is the joint exercise between the armies of two countries.
- Eastern Bridge is the joint exercise between the air forces of two countries.
- Oman also provides critical operational support to Indian naval deployments in the Arabian sea for anti-piracy missions.
- Oman also actively participates in the Indian Ocean Naval Symposium (IONS).
- India has supplied rifles to Oman. Also, India is considering setting up a defence production unit in Oman.
- Oman is India’s closest defence partner in the Gulf region and an important anchor for India’s defence and strategic interests.
- Access to Port of Duqm in Oman:
- In a strategic move to expand its footprint in the Indian Ocean region, India has secured access to the key Port of Duqm in Oman for military use and logistical support.
- This is part of India’s maritime strategy to counter Chinese influence and activities in the region.
- The Port of Duqm is situated on the southeastern seaboard of Oman, overlooking the Arabian Sea and the Indian Ocean.
- It is strategically located, in close proximity to the Chabahar port in Iran. With the Assumption Island being developed in Seychelles and Agalega in Mauritius, Duqm fits into India’s proactive maritime security roadmap.
Ex Cobra Warrior 22
Why in News?
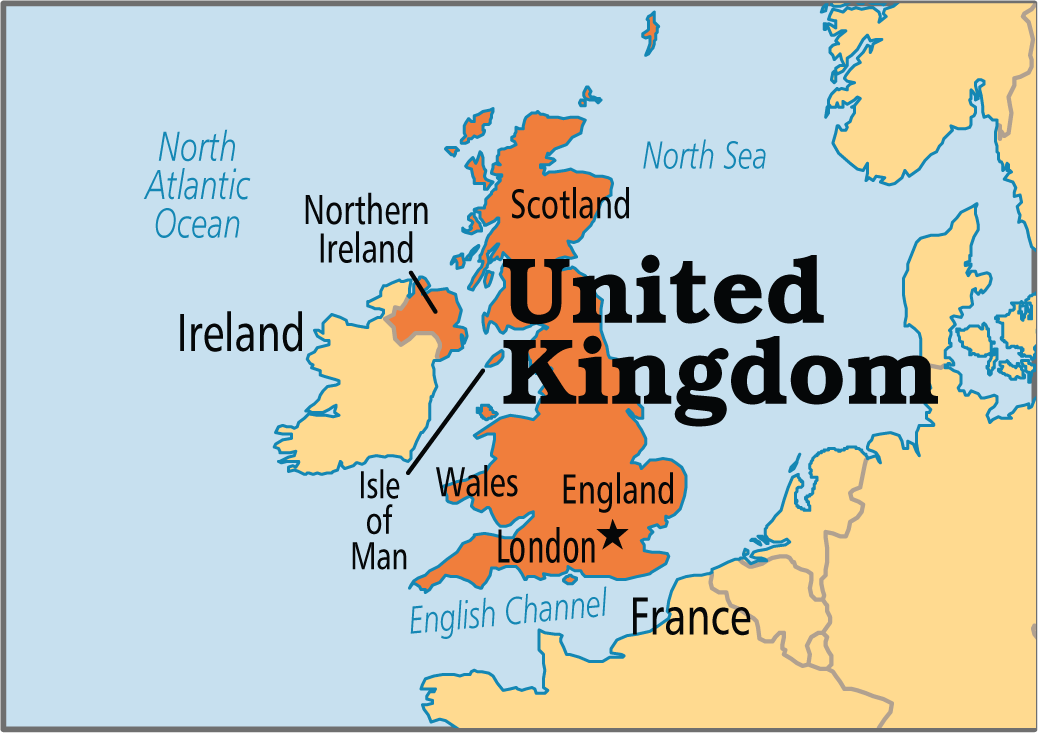
The Indian Air Force will participate in the multi-nation Air Exercise named 'Ex Cobra Warrior 22' at Royal Air Force Base in Waddington, United Kingdom.
- Five indigenous LCA (Light Combat aircraft) Tejas fighter aircraft will participate in the exercise and a C-17 aircraft will provide transport support.
What are the Key Points?
- About Ex Cobra Warrior 22: It is one of the largest annual Royal Air Force exercises (United Kingdom) and aims to train both pilots and other air specialists in planning and executing complex airborne missions.
- Other Joint Exercises between India and the UK: