National Cyber Security Strategy 2020 | 04 Mar 2021
Why in News
A National Cyber Security Strategy 2020 is being formulated by the Office of National Cyber Security Coordinator at the National Security Council Secretariat.
- Cyber Security is protecting cyber space including critical information infrastructure from attack, damage, misuse and economic espionage.
- The National Security Council (NSC) of India is a three-tiered organization that oversees political, economic, energy and security issues of strategic concern.
Key Points
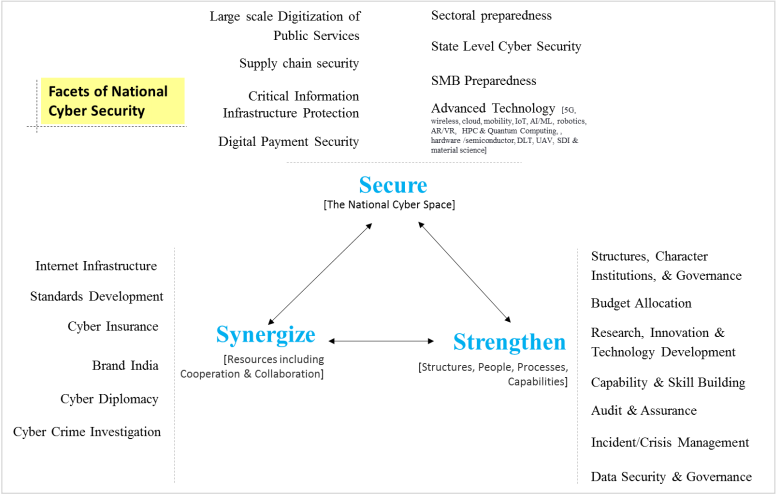
- National Cyber Security Strategy 2020:
- Aim:
- To improve cyber awareness and cybersecurity through more stringent audits. Empanelled cyber auditors will look more carefully at the security features of organisations than are legally necessary now.
- About:
- There will be table-top cyber crisis management exercises regularly to reinforce the idea that cyber attacks can take place regularly.
- It does call for an index of cyber preparedness, and attendant monitoring of performance.
- A separate budget for cybersecurity is suggested, as also to synergise the role and functions of various agencies with the requisite domain knowledge.
- Aim:
- Need:
- Cyber warfare offensives:
- The United States is just one of many countries that have invested significant amounts of money in developing not just defences against attack, but the ability to mount damaging cyber warfare offensives.
- The countries which are believed to have the most developed cyber warfare capabilities are the United States, China, Russia, Israel and the United Kingdom.
- Increased Digital usage Post-Covid:
- Critical infrastructure is getting digitised in a very fast way — this includes financial services, banks, power, manufacturing, nuclear power plants, etc.
- For Protecting Critical Sectors:
- It is particularly significant given the increasing interconnectedness of sectors and proliferation of entry points into the internet, which could further grow with the adoption of 5G.
- There were 6.97 lakh cyber security incidents reported in the first eight months of 2020, nearly equivalent to the previous four years combined, according to information reported to and tracked by Indian Computer Emergency Response Team (CERT-In).
- Recent Cyber Attacks:
- There has been a steep rise in the use of resources like malware by a Chinese group called Red Echo to target “a large swathe” of India’s power sector.
- Red Echo used malware called ShadowPad, which involves the use of a backdoor to access servers.
- Chinese hacker group known as Stone Panda had “identified gaps and vulnerabilities in the IT infrastructure and supply chain software of Bharat Biotech and the Serum Institute of India.
- SolarWinds hack, impacted national critical infrastructure in the USA.
- There has been a steep rise in the use of resources like malware by a Chinese group called Red Echo to target “a large swathe” of India’s power sector.
- For Government:
- A local, state or central government maintains a huge amount of confidential data related to country (geographical, military strategic assets etc.) and citizens.
- For Individuals:
- Photos, videos and other personal information shared by an individual on social networking sites can be inappropriately used by others, leading to serious and even life-threatening incidents.
- For Businesses:
- Companies have a lot of data and information on their systems. A cyber attack may lead to loss of competitive information (such as patents or original work), loss of employees/customers’ private data resulting into complete loss of public trust on the integrity of the organization.
- Cyber warfare offensives:
- Present Government Initiatives:
Way Forward
- India is the second-fastest digital adapter among 17 of the most-digital economies globally, and rapid digitisation does require forward-looking measures to boost cybersecurity.
- It is important for the corporates or the respective government departments to find the gaps in their organisations and address those gaps and create a layered security system, wherein security threat intelligence sharing is happening between different layers.
- There is a need for an apex body to ensure operational coordination amongst various agencies and ministries.
- Cyber deterrence can be envisaged on the lines of strategic deterrence to dissuade cyberattackers. We need to acquire offensive capabilities for effective deterrence in cyberspace.