Governance
New VPN Rules
- 28 Jun 2022
- 9 min read
For Prelims: VPN, CERT-In, IP Address
For Mains: Working of VPN, New VPN Rules, IT and Computers.
Why in News?
Recently, Indian Computer Emergency Response Team (CERT-In) issued norms under which VPN providers have to record personal information of their customers, including the purpose of using the service, for five years.
- CERT-In is an organisation of the Ministry of Electronics and Information Technology with the objective of securing Indian cyberspace.
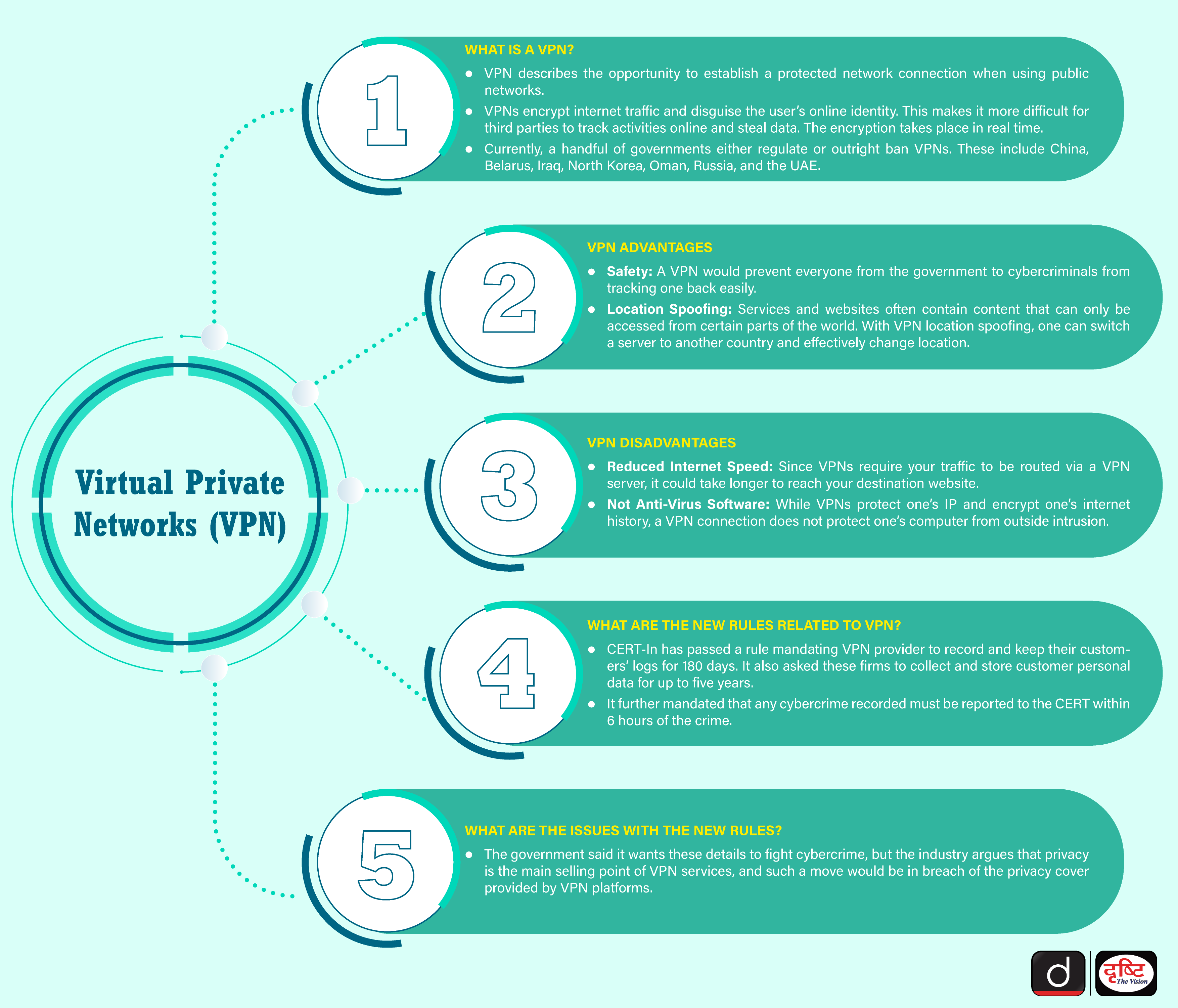
What is VPN?
- About:
- VPN stands for "Virtual Private Network" and describes the opportunity to establish a protected network connection when using public networks.
- VPNs encrypt internet traffic and disguise the user’s online identity. This makes it more difficult for third parties to track activities online and steal data. The encryption takes place in real time.
- Functioning:
- A VPN hides the user’s IP address by letting the network redirect it through a specially configured remote server run by a VPN host.
- This means that if a user is surfing online with a VPN, the VPN server becomes the source of data.
- Internet Service Provider (ISP) and other third parties cannot see which websites the user visits or data sent and received online.
- A VPN hides the user’s IP address by letting the network redirect it through a specially configured remote server run by a VPN host.
- Benefits:
- Secures encryption:
- A VPN connection disguises data traffic online and protects it from external access.
- Unencrypted data can be viewed by anyone who has network access. With a VPN, the government, hackers and cyber criminals can’t decipher this data.
- Access to regional content:
- Regional web content is not always accessible from everywhere. Services and websites often contain content that can only be accessed from certain parts of the world. Standard connections use local servers in the country to determine your location.
- With VPN location spoofing, one can switch a server to another country and effectively change location.
- Secure data transfer:
- VPN services connect to private servers and use encryption methods to reduce the risk of data leakage providing secured passage for data.
- Secures encryption:
- Limitations:
- Reduced Internet Speed: Since VPNs require your traffic to be routed via a VPN server, it could take longer to reach your destination website.
- Not Anti-Virus Software: VPNs do not function like comprehensive anti-virus software. While they protect one’s IP and encrypt one’s internet history, a VPN connection does not protect one’s computer from outside intrusion.
- Once the malware has found its way to a device, it can steal or damage the data, whether VPN is in service or not.
- Regulation:
What are the New Rules related to VPN?
- The Union Ministry of Electronics and Information Technology issued new norms for VPN companies to record personal information of their users including names, email id, phone number and IP address for a period of five years.
- They also have to record usage patterns, purpose of hiring services and various other information.
- Apart from VPN companies, data centers, virtual service network providers, cloud service providers have also been asked to record and maintain similar data.
- Entities are also required to report cybersecurity incidents to CERT-In within six hours of becoming or being made aware of them.
Why has the government issued these rules?
- These rules will “enhance overall cyber security posture and ensure safe & trusted internet in the country”.
- It noted that the Indian Computer Emergency Response Team (CERT-In), which serves as a safeguard against cyber-attacks, has identified “gaps” in the way it analyses online threats due to which it has issued the new norms for reporting cyber incidents.
- In 2021, a Parliamentary Standing Committee, in a report to the Rajya Sabha, wanted the Ministry to block VPNs with assistance from internet service providers.
What are the related Issues?
- Customers will have to go through a stringent KYC process while signing up to use a VPN and will have to state the purpose of using the services.
- With the new rules the government will basically have access to the personal information of the customers which makes the use of a VPN redundant.
- Many VPN providers are mulling the implications of the new rules and some have even threatened to pull back their service from the country.
- In response to CERT-In rules, Nord VPN, one of the world’s largest VPN providers, has said it is moving its servers out of the country. Two other firms, Express VPN and Surfshark, said they will shut down their physical servers in India and cater to users in India through virtual servers located in Singapore and UK.
What is a Virtual Server?
- About:
- A Virtual Server is a simulated server environment built on an actual physical server. It recreates the functionality of a dedicated physical server.
- It uses resources of the physical server. Multiple virtual servers can run on a single physical server.
- Key Points:
- Efficiency:
- Converting one physical server into multiple virtual servers allows organizations to use processing power and resources more efficiently by running multiple operating systems and applications on one partitioned server.
- Cost Reduction:
- Virtualization also reduces cost as maintaining a virtual server infrastructure is low compared to physical server infrastructure.
- Security:
- Virtual servers also offer higher security than a physical server infrastructure as the operating system and applications are enclosed in a virtual machine.
- This helps contain security attacks and malicious behaviors inside the virtual machine.
- Testing:
- Virtual servers are also useful in testing and debugging applications in different operating systems and versions without having to manually install and run them on several physical machines.
- Efficiency:
UPSC Civil Services Examination, Previous Year Question
Q. What is “Virtual Private Network”? (2011)
(a) It is a private computer network of an organization where the remote users can transmit encrypted information through the server of the organization.
(b) It is a computer network across a public internet that provides users access to their organization’s network while maintaining the security of the information transmitted.
(c) It is a computer network in which users can access a shared pool of computing resources through a service provider.
(d) None of the statements (a), (b) and (c) given above is a correct description of Virtual Private Network.
Ans: (b)






-min.jpg)